The Quantum Leap in Cryptography: NIST’s Path to Securing Our Digital Future
In an era where digital security faces unprecedented challenges, the emergence of quantum computing has sparked both excitement and concern within cybersecurity. As quantum computers grow more powerful, they threaten to crack the modern encryption systems that protect our digital infrastructure. This article will explore how the National Institute of Standards and Technology (NIST) is leading the charge and developing quantum-resistant cryptographic standards that will secure our personal and national data.
Understanding NIST: Golden Standards
NIST is a U.S. agency focused on research, innovation, and the development of critical scientific standards. In today’s digital landscape, NIST plays a crucial role in cybersecurity by developing the standards and guidelines that protect information systems against threats to the confidentiality, integrity, and availability of information. NIST’s influence extends far beyond U.S. borders. Its standards are adopted globally, making it one of the most influential organizations in establishing cybersecurity practices worldwide. Unlike regulatory agencies that enforce rules, NIST creates voluntary standards through collaborative processes involving industry, academia, and government stakeholders—as you’ll read in today’s article. This collaborative approach ensures that standards are both technically sound and practically implementable. NIST openly publishes their research and development in what is called FIPS.
FIPS: Framework for Federal Information Security
Federal Information Processing Standards, commonly known as FIPS, form the backbone of the U.S. government’s approach to information security. These standards, developed by NIST, establish requirements for federal agencies and contractors for protecting sensitive information. While developed primarily for government use, FIPS standards have become de facto standards for many industries worldwide, especially those handling sensitive information such as PII or HIPAA-protected data.
FIPS-140, for example, dates back to 1994 and has since been revised twice, creating FIPS 140-3, which specifies security requirements and compliance for cryptographic modules used in computer systems today. Compliance with this standard ensures that cryptographic tools used by government agencies meet minimum security requirements. Similarly, FIPS 197 established the Advanced Encryption Standard (AES), revised in 2023, which has become one of the most widely used symmetric encryption algorithms worldwide.
The significance of FIPS extends beyond technical specifications. When NIST incorporates a cryptographic algorithm into FIPS, it signals to the global community that the algorithm has undergone rigorous testing and analysis. This validation process gives organizations strong confidence, helping to establish a baseline of trust in digital security.
Why does Quantum Computing pose a Challenge?
Before diving deeper into NIST’s quantum-resistant standards, it’s essential to understand why quantum computing poses such a significant threat to current cryptographic systems. Unlike classical computers that use bits (0s and 1s) as their fundamental units of information, quantum computers use quantum bits, or “qubits.”1 Thanks to quantum mechanical properties like superposition and entanglement, qubits can exist in multiple states simultaneously, enabling quantum computers to solve certain problems exponentially faster than classical computers.
This quantum advantage becomes particularly problematic for cryptography when considering algorithms like RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography), which currently form the foundation of secure internet communications today. These algorithms rely on the computational difficulty of factoring large numbers or solving discrete logarithm problems—tasks that would take classical computers millions of years to complete but could potentially be solved by sufficiently powerful quantum computers in a matter of hours or days.
Shor’s algorithm, developed by mathematician Peter Shor in 1994, demonstrated theoretically that quantum computers could efficiently factor large numbers, essentially breaking RSA encryption. While large-scale quantum computers capable of implementing Shor’s algorithm don’t yet exist, steady progress in quantum computing has made the threat increasingly tangible, creating an urgent need for quantum-resistant cryptographic solutions.
NIST’s Post-Quantum Cryptography Standardization Process
Recognizing the looming threat, NIST launched its Post-Quantum Cryptography Standardization Process in 2016.2 This initiative aimed to develop, evaluate, and standardize one or more quantum-resistant public-key cryptographic algorithms. Unlike previous standardization efforts, this process needed to address threats that hadn’t fully materialized yet, requiring NIST to balance theoretical security analysis with practical implementation considerations.
The standardization process began with a call for proposals, to which the cryptographic community responded enthusiastically. NIST assessed 82 algorithms from researchers, organizations, and cryptographers worldwide, spanning various mathematical approaches. These proposed algorithms underwent rigorous analysis through three rounds of evaluation, with each round narrowing the field based on security, performance, and implementation characteristics.
Timeline: NIST’s Quantum-Resistant Journey
Announcement
NIST announced the Post-Quantum Cryptography Standardization Process, calling for algorithm submissions.
Initial Submission
The initial submission period closed with 69 eligible algorithms, beginning the first round of public evaluation.
Second Round
NIST announced 26 algorithms that advanced to the second round.
Finalists
15 candidates advanced to the third round, with 7 designated as finalists and 8 as alternates.
First Official 4 Algorithms3
NIST announced the first four quantum-resistant cryptographic algorithms: CRYSTALS-Kyber for general encryption and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures.
5th Algorithm Added4
NIST selected HQC (Hamming Quasi-Cyclic) as the fifth algorithm for post-quantum encryption.
Alongside the algorithms, NIST has been developing their standardizations.
Timeline: NIST FIPS Standardizations
First 3 Draft FIPS
NIST released 3 draft FIPS for public comment.
First 3 Finalized FIPS5
NIST released the first 3 finalized post-quantum encryption standards—FIPS 203 (CRYSTALS-Kyber), 204 (CRYSTALS-Dilithium), and 205 (SPHINCS+)—marking a significant milestone in preparing these algorithms for widespread implementation.
FIPS 206
NIST to release draft and final FIPS 206 (for FALCON).
FIPS 207
NIST to release draft and final FIPS 207 (for HQC).
This methodical approach demonstrates NIST’s commitment to thorough evaluation, ensuring that the selected algorithms provide strong security guarantees while remaining practical for real-world implementation.
The Quantum-Resistant Algorithms
The algorithms selected by NIST represent diverse mathematical approaches, providing defense-in-depth against potential vulnerabilities:
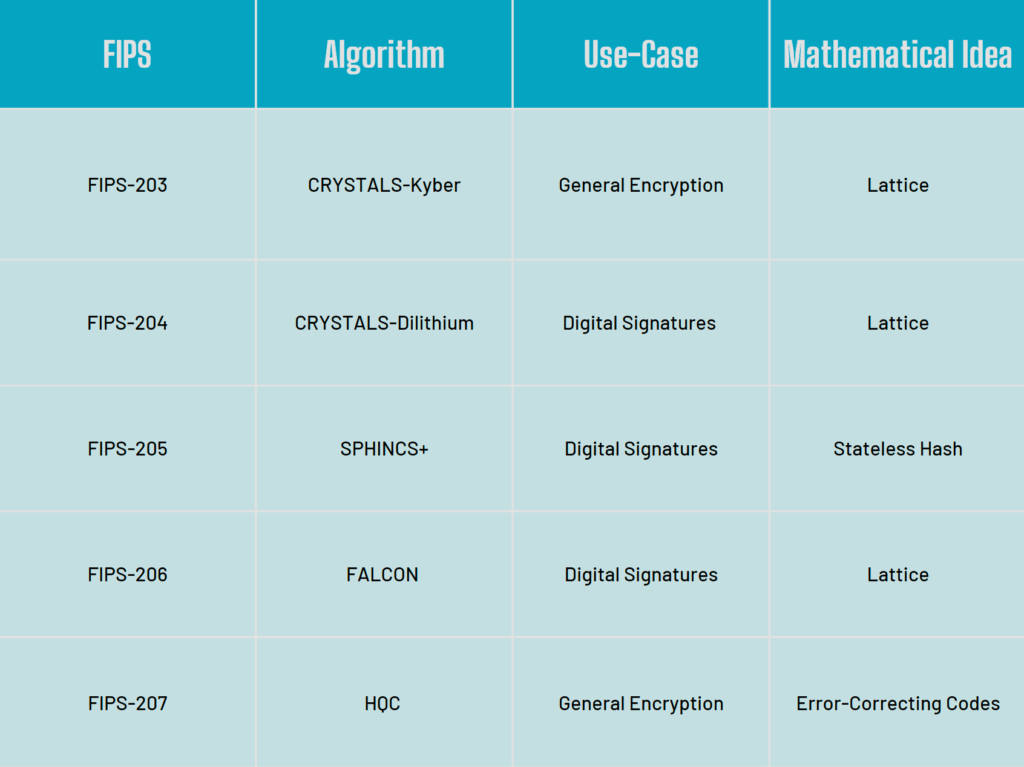
CRYSTALS-Kyber: Selected for general encryption, Kyber uses a lattice-based approach. Lattice-based cryptography relies on the difficulty of solving certain mathematical problems involving lattices-geometric structures in multi-dimensional space. Kyber offers an excellent balance between key size and security, making it suitable for widespread deployment.
CRYSTALS-Dilithium: A digital signature algorithm also based on lattice problems. Digital signatures verify the authenticity of digital messages or documents, providing assurance that information hasn’t been altered and confirming the sender’s identity.
FALCON: Another lattice-based signature algorithm that offers smaller signatures than Dilithium but requires more complex implementation. This provides implementers with options depending on their specific needs.
SPHINCS+: Unlike the lattice-based algorithms, SPHINCS+ uses stateless hash functions as its foundation. Hash-based signatures are among the most conservative choices, being both slower and larger, with security proofs that require fewer assumptions than other approaches.
HQC: The most recently selected algorithm uses code-based cryptography, an approach based on error-correcting codes. This addition diversifies NIST’s portfolio, ensuring that the standards don’t rely exclusively on a single mathematical foundation.
By selecting algorithms based on different mathematical problems, NIST ensures that a breakthrough in solving one type of problem wouldn’t compromise all post-quantum security simultaneously.
Implementation Challenges and Transition Strategies
While developing quantum-resistant algorithms represents a significant achievement, implementing them across global digital infrastructure presents enormous challenges. The new algorithms often require more computational resources and larger key sizes than current standards. Organizations must carefully plan their transition to maintain security without disrupting operations.
NIST recommends a phased approach, beginning with cryptographic agility—the ability to quickly replace algorithms without major system redesigns. This involves implementing “hybrid” solutions that use both traditional and post-quantum algorithms together, ensuring compatibility with existing systems while adding quantum resistance.
The process will likely take years, with critical infrastructure and long-lived data requiring the earliest attention. Data that must remain confidential for decades needs protection now, as adversaries might capture encrypted information today and decrypt it later when quantum computers become more powerful—a threat known as “harvest now, decrypt later.”
The Broader Implications
The development of quantum-resistant cryptography illustrates how technological advancement often creates a security paradox—the same innovations that drive progress can also undermine existing security measures. Quantum computing promises revolutionary advances in fields ranging from medicine to materials science, potentially solving problems that have defeated classical computers. Yet this same power threatens the cryptographic foundations of our digital society.
This paradox underscores the importance of proactive security planning. By developing quantum-resistant standards before large-scale quantum computers arrive, NIST helps ensure that the beneficial aspects of quantum technology can be realized without compromising digital security.
Conclusion
NIST’s work on post-quantum cryptography exemplifies how standards organizations can address emerging technological challenges through collaborative, transparent processes. By bringing together experts from around the world, rigorously evaluating proposed solutions, and developing implementable standards, NIST is helping to secure our digital future against quantum threats.6
As quantum computing continues to advance, the cryptographic community must remain vigilant, continuously analyzing and refining quantum-resistant algorithms. The standardization of these algorithms doesn’t mark the end of the journey but rather the beginning of a new era in cryptography—one in which security assumptions must be regularly reassessed in light of quantum progress.
For organizations and individuals alike, understanding the basics of quantum cryptography has become increasingly important. While the mathematics behind these algorithms may remain the domain of specialists, appreciating the nature of the quantum threat and the strategies for addressing it enables informed decision-making about digital security in an era of technological transformation.
Want to dive deeper into cybersecurity as a whole?
If you’re interested in exploring more about the future of cybersecurity and other upcoming trends, check out my article on The Future of Cybersecurity.
- IBM. “What Is Quantum Computing?” IBM, 5 Aug. 2024, https://www.ibm.com/think/topics/quantum-computing. ↩︎
- National Institute of Standards and Technology. “Post-Quantum Cryptography.” Computer Security Resource Center, 03 Jan. 2017, https://csrc.nist.gov/projects/post-quantum-cryptography. ↩︎
- NIST Announces First Four Quantum-Resistant Cryptographic Algorithms. 5 July 2022, https://www.nist.gov/news-events/news/2022/07/nist-announces-first-four-quantum-resistant-cryptographic-algorithms. ↩︎
- NIST Selects HQC as Fifth Algorithm for Post-Quantum Encryption. 11 Mar. 2025, https://www.nist.gov/news-events/news/2025/03/nist-selects-hqc-fifth-algorithm-post-quantum-encryption. ↩︎
- NIST Releases First 3 Finalized Post-Quantum Encryption Standards. 13 Aug. 2024, https://www.nist.gov/news-events/news/2024/08/nist-releases-first-3-finalized-post-quantum-encryption-standards. ↩︎
- National Institute of Standards and Technology. “What Is Post-Quantum Cryptography?” NIST, 10 Apr. 2025, https://www.nist.gov/cybersecurity/what-post-quantum-cryptography. ↩︎