As cyber threats continue to evolve in complexity and frequency, staying informed on current risks and emerging trends is paramount for cybersecurity professionals. In this comprehensive exploration, we will delve into the multifaceted landscape of cybersecurity, examining both the prevailing risks and the transformative trends shaping its future. Continuous education and collaboration among cybersecurity practitioners have become indispensable, fostering collective resilience against the ever-evolving threat landscape.
Amidst the proliferation of identity theft and credential-based attacks, Identity and Access Management (IAM) transcends mere authentication. IAM encompasses identity lifecycle management, privilege management, and risk-based access controls to fortify defenses against evolving cyber threats. As businesses embark on digital transformation journeys, IAM emerges not only as a defensive mechanism but also as an enabler of seamless user experiences and operational efficiency. Conversely, the use of Artificial Intelligence (AI) can enhance common threats by scaling, automating, and generating different forms of content. Furthermore, AI has become the incubator of new threats, such as adversarial machine learning, which maliciously fools an AI model and can be a new leading concern for cybersecurity.
Current Risks in Cybersecurity
The World Economic Forum’s (WEF) Global Cybersecurity Outlook 2024,1 produced in collaboration with Accenture, examined the cybersecurity trends that will affect economies and societies in the years to come, highlighting the widening cyber inequity.
In its most recent report, WEF illustrated that over 1 in 3 respondents see the lack of trained specialists as the main barrier to achieving cyber-resilience objectives. Shockingly, 78% of them reported a lack of in-house cybersecurity skills needed to achieve their goals. What’s truly concerning is that 57% (according to the 2023 ISC2 Cybersecurity Workforce Study) of cyber professionals believe that the staff shortage in cybersecurity is a moderate to extreme threat.2
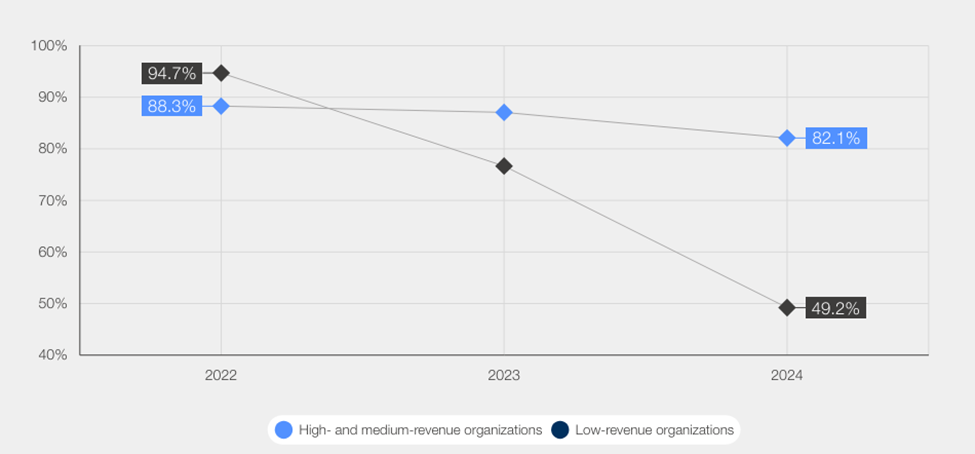
Furthermore, inequities in skills gaps are evident across organizations of varying sizes. As highlighted by the WEF, 31% of leaders from smaller revenue organizations reported missing critical people and skills. In contrast, only 11% of leaders from the largest organizations stated similar challenges. Budget constraints amplify the shortage of cybersecurity talent, with 34% of respondents attributing the shortfall to financial limitations as the leading cause, according to the ISC2 cybersecurity workforce study.
Strategies to Address experience Gaps
Organizations find different approaches to recovering the gaps in cybersecurity personnel and knowledge. Particularly, 33% of recruiters are desperate to find professional cybersecurity workers; meanwhile, 41% of organizations look to up-skill their employees to fulfill outstanding positions. Furthermore, cybersecurity training and certifications are of utmost importance for 91% of organizations, indicating a strong effort to strengthen their cybersecurity workforce.
Nevertheless, micro-credentials (or company badging) and apprentice programs are less explored by most companies. Very few of the organizations, 9%, are prepared for a learning and development approach related to micro-credentials, and a mere 8% seem to have adopted apprentice programs. These discrepancies show that many cybersecurity roles have a university degree or traditional certification requirement. Possibly, this could indicate the need for alternative non-university routes for talent pipelines in cybersecurity, specifically with mentorship or on-the-job training.
Even with the focus on cybersecurity, most companies continue to grapple with it as a critical issue, falling short in either funding, educating, or training their workforce.
Emerging Trends in Identity and Access Management
As organizations increasingly rely on digital systems and cloud services, the landscape of IAM is rapidly evolving. This section explores the latest trends shaping IAM practices and their impact on security and user experience.
Decentralized Identity (DID) & Self-Sovereign Identity (SSI)
DID and SSI represent a paradigm shift in digital identity management. Within these models, individuals have control over their online identities. These practices lower interdependency with central authorities, thereby promoting privacy and security.
Zero Trust Architecture (ZTA)
ZTA is the frontrunner of a massive change in IAM, moving away from traditional perimeter-based security models to a risk-based approach. Based on the idea of least privilege, it reduces attack vectors and protects assets. By adopting ZTA principles, organizations can minimize the risk of unauthorized access and lateral movement within their networks.
Passwordless Authentication
Passwordless authentication emerges as a promising alternative to traditional password-based methods, enhancing security while streamlining user experience. This comes by replacing the password with additional measures from something you ‘are’ (biometrics), such as a fingerprint, or something you ‘have’, such as a push notification to your mobile device. However, the rush to adopt generative AI and other emerging technologies poses challenges in securing legacy technology, underscoring the need for stronger cybersecurity foundations.
The Influence of Generative AI on Cybersecurity
“…This year, approximately half of leaders still agree that generative AI will have the most significant impact on cybersecurity in the next two years” (WEF). Generative AI emerges as a significant focus, with leaders across various industries, including cybersecurity, agriculture, banking, and insurance, citing it as the most influential factor. Critical infrastructure, like energy technology, energy utilities, and oil and gas, boasts a 94% confidence level of being minimally cyber-resilient. Critical infrastructure is a key pressure point we’ll discuss in another article.
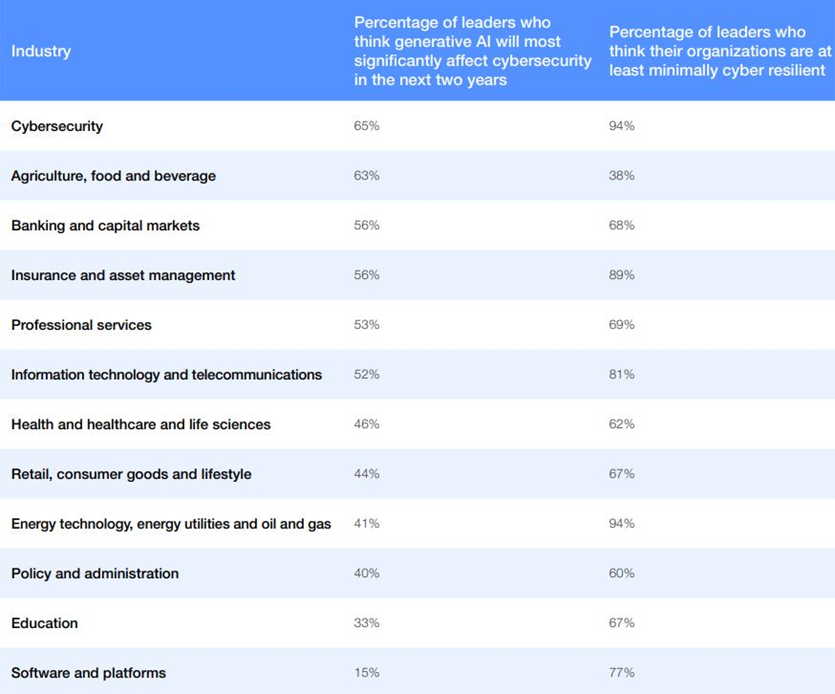
Importance of Cybersecurity Foundations
The significance of robust cybersecurity foundations cannot be overstated. In recent incidents, MGM endured a 10-day critical disruption after a social engineering attack that took place during a ten-minute phone call.3 Additionally, securing legacy technology remains a primary challenge for 44% of the largest organizations by revenue, necessitating concerted efforts to modernize and fortify systems.
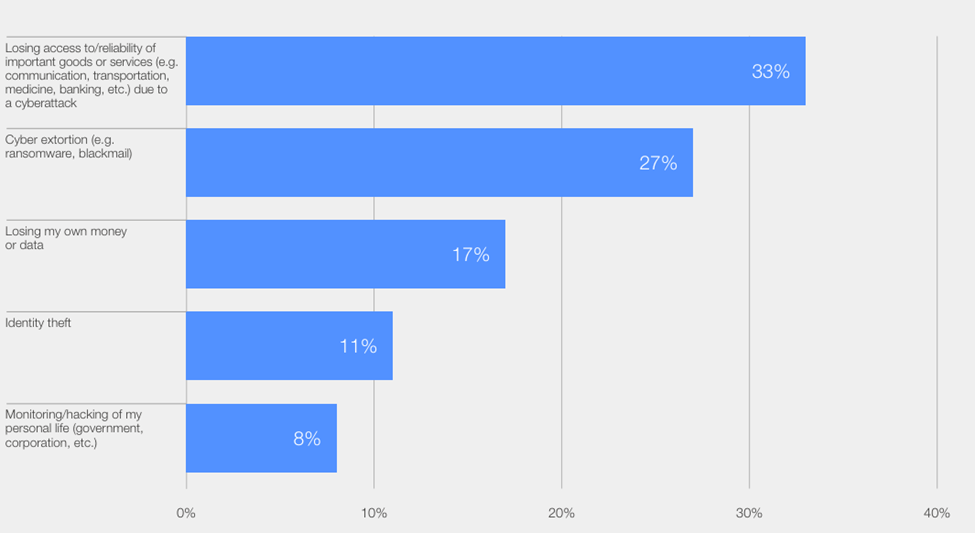
Conclusion
IAM remains a cornerstone of cybersecurity, surpassing the humble beginnings of authentication. Issues around shortage of skilled cybersecurity professionals poses a significant challenge, necessitating new strategies such as up-skilling, micro-credentials, and apprenticeship programs to bridge the gap. By addressing current challenges and embracing emerging trends, cybersecurity professionals can enhance organizational resilience.
Collaboration and innovation will be essential as organizations navigate the complexity of geopolitical dynamics and technological advancements in IAM. As the digital realm expands and cyber threats become increasingly sophisticated, the role of IAM in safeguarding critical assets will only continue to grow in importance. By embracing innovation, fostering collaboration, and staying vigilant, organizations can fortify their defenses and navigate the complexities of the digital age with confidence.
- “Global Cybersecurity Outlook 2024.” World Economic Forum, 11 Jan. 2024, www.weforum.org/publications/global-cybersecurity-outlook-2024/. ↩︎
- ISC2. “ISC2 Cybersecurity Workforce Study, 2023.” ISC2 Inc., 2023. www.isc2.org/-/media/Project/ISC2/Main/Media/documents/research/ISC2_Cybersecurity_Workforce_Study_2023.pdf?rev=28b46de71ce24e6ab7705f6e3da8637e&hash=CE6762D811935593F5C04AAB49DF33DF. ↩︎
- Braithwaite, Sarah. “ALPHV: Hackers Reveal Details of MGM Cyber Attack.” Westoahu Cybersecurity, 24 Oct. 2023, westoahu.hawaii.edu/cyber/global-weekly-exec-summary/alphv-hackers-reveal-details-of-mgm-%20cyber-attack/. ↩︎